Unlocking Robust Security: Advanced Encryption Practices for ICS/OT Environments
Securing sensitive data and communications in industrial control systems (ICS) and Operational Technology (OT) cannot be overstated. It is not just a matter of maintaining the integrity and availability of industrial operations but also a crucial step in the fight against unauthorized access and cyber threats. This article delves into the best encryption practices across different Purdue Model levels, discusses appropriate encryption algorithms, and suggests implementation strategies on various devices within industrial networks.
Overview of Encryption in ICS/OT Environments
Encryption in industrial environments involves securing data at rest and in transit. The choice of encryption methods and their implementation is guided by industrial systems' specific requirements and constraints, including real-time performance, safety, and operational continuity.
Implementing encryption in Industrial Control Systems (ICS) and Operational Technology (OT) environments is challenging. It's a critical component of a comprehensive cybersecurity strategy, safeguarding sensitive operational data and maintaining the integrity and confidentiality of communication within industrial networks. However, the complexities and nuances of implementing encryption in these specialized environments are worth exploring.
Challenges and Requirements
Real-Time Constraints
Many ICS and OT systems operate in real-time or near-real-time environments where any delay, even milliseconds, can affect system performance and potentially lead to hazardous situations. Thus, encryption methods must be efficient and lightweight, imposing minimal latency.
Legacy Systems
Many industrial environments include legacy systems that must be designed with modern cybersecurity practices in mind. These systems might need more computational power to handle standard encryption protocols, making integrating encryption particularly challenging.
Diverse and Disparate Technologies
Industrial environments typically feature a heterogeneous mix of devices from different vendors and generations, each with varying capabilities and security features. Achieving consistent encryption across all these systems requires careful planning and sometimes custom solutions.
Regulatory and Compliance Requirements
Different industries have specific regulations that govern data protection and privacy (e.g., NERC CIP for the energy sector in the United States). Encryption practices must comply with these regulatory requirements, adding another layer of complexity to their implementation.
Encryption Strategies by ICS Layers
To address these challenges, tailored encryption strategies must be developed for each layer of the Purdue Model, considering the operational characteristics and constraints of the devices at each level.
When implementing encryption strategies in Industrial Control Systems (ICS) and Operational Technology (OT), it is crucial to consider each layer's specific needs and constraints in the Purdue Model.
This model, which organizes network architecture into several discrete layers from the plant floor to the enterprise level, helps delineate where certain cybersecurity practices, like encryption, are most appropriate and effective. Here's a deeper dive into encryption practices suited for each level.
The Purdue Model of Industrial Control Systems provides a layered framework that is useful for understanding where and how to apply encryption technologies:
Levels 0 and 1 (Physical and Basic Control)
Devices Involved
These levels include devices directly interacting with the physical process, such as sensors, actuaries, and primary programmable logic controllers (PLCs).
Encryption is typically not applied at this level due to the devices' real-time nature and low computational capabilities.
However, secure communication protocols like OPC UA can be used when higher security is needed, especially for devices capable of handling such overhead.
Encryption Challenges
Performance Constraints
Devices at these levels typically have limited processing power and operate under stringent real-time constraints. Introducing encryption directly into these devices might impact their operational efficiency.
Legacy Systems
Many devices at these levels are older and were not designed with modern security features, including the capability to handle encryption.
Recommended Practices
Peripheral Encryption
Instead of direct encryption within devices, use gateways or edge devices that can preprocess and encrypt data before it is transmitted to higher network levels or stored. This approach reduces the computational burden on field devices.
Secure Network Segmentation
Implement encrypted tunnels or VPNs between these devices and the gateways or higher-level systems to protect data in transit without modifying the device firmware.
Level 2 (Area Supervisory Control):
Devices Involved
More sophisticated PLCs, remote terminal units (RTUs), and other control systems that manage multiple devices or a section of the plant.
Strategy
Implement lightweight encryption protocols and secure communication channels. Protocols like MQTT with SSL/TLS can be used for encrypted communications, which the devices support. For others, consider using intermediate devices that aggregate and encrypt data before it is sent to higher levels or external networks.
Encryption
For devices that support it, lightweight encryption methods are recommended to protect communications without impacting system performance.
Examples include using TLS for network communications or applying encrypted tunnels for remote access.
Encryption Challenges
Intermediate Complexity
Devices at this level are more capable than those at Levels 0 and 1, but they may still not efficiently handle heavy computational tasks.
Recommended Practices
Lightweight Encryption Protocols
Use protocols for constrained environments, such as MQTT with SSL/TLS, for secure messaging.
Enhanced Device Capabilities
Upgrade firmware or hardware to support basic encryption for sensitive control commands and data transmission.
Level 3 (Site Operations):
Devices Involved
This level includes systems like SCADA (Supervisory Control and Data Acquisition), which monitor and control industrial processes across the site, and MES (Manufacturing Execution Systems), which manage production on a larger scale.
Encryption Challenges
Higher Data Volumes
The volume and sensitivity of data managed at this level are significantly higher, necessitating robust encryption to protect against breaches.
Recommended Practices
End-to-End Encryption
Implement comprehensive encryption strategies for all data in transit and at rest. This includes using established cryptographic protocols like TLS for network communication and AES for storing data.
Regular Security Assessments
Continuously evaluate the encryption standards and protocols to ensure they meet the latest security best practices and compliance requirements.
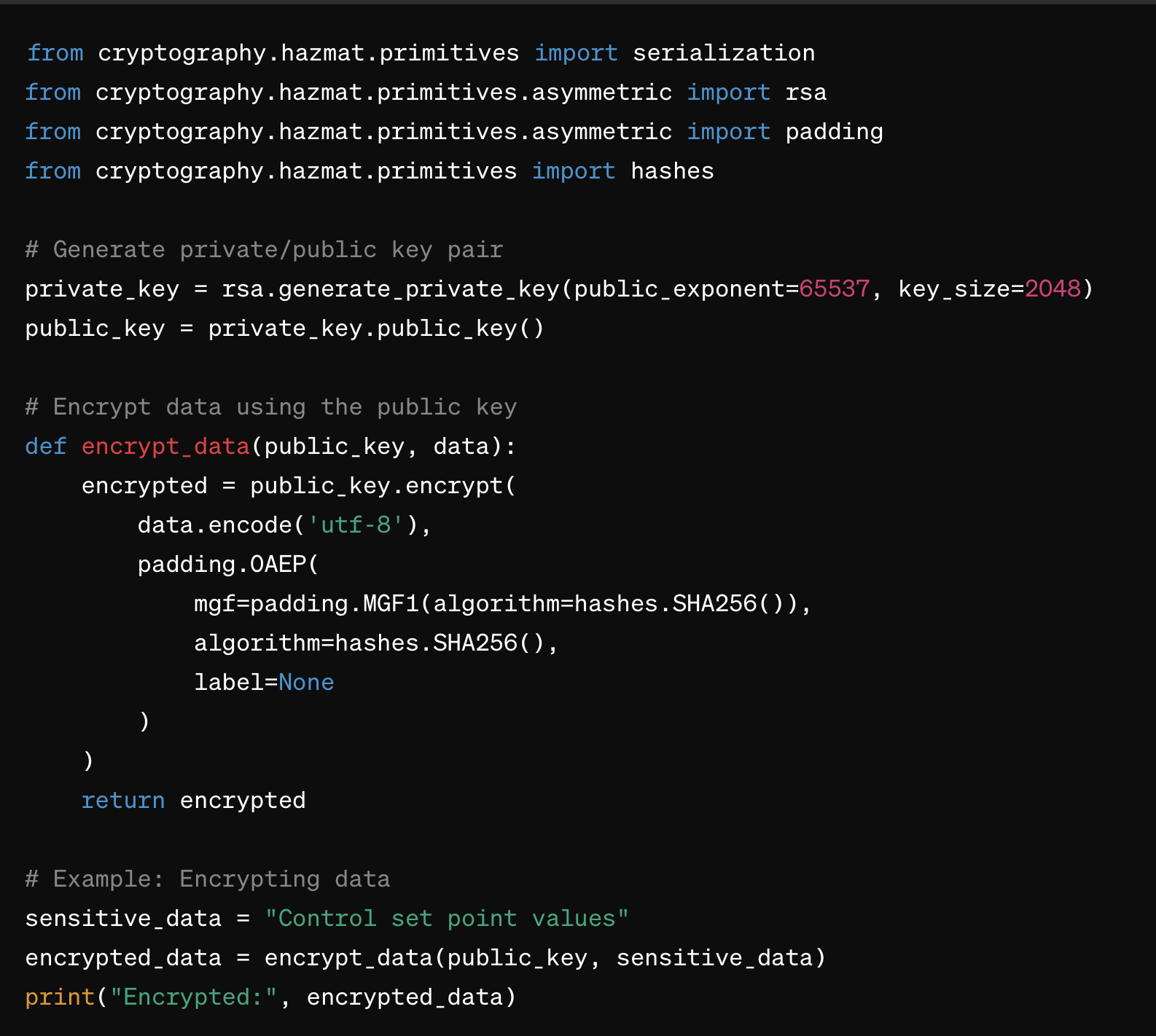
This Python example demonstrates how to encrypt sensitive data using RSA public-key cryptography, suitable for environments like Level 3 where there is less concern about the computational overhead of encryption.
Level 4 (Enterprise Management)
Devices Involved
Enterprise-level servers, database systems, and other resources handle business and production planning, logistics, and external communications.
Encryption Challenges
High Complexity and Regulation
Data at this level often includes personally identifiable information (PII), financial data, and other information that could be subject to regulatory compliance requirements.
Recommended Practices
Advanced Encryption Standards
Use the highest available encryption standards, such as AES-256 for data at rest and TLS 1.3 for data in transit.
Comprehensive Policy Management
Establish and enforce policies regarding data encryption, key management, and encryption at rest and in transit to ensure that all data handled at this level is encrypted.
Encryption Algorithms Used
Encryption algorithms are fundamental to securing data in industrial settings, particularly within Industrial Control Systems (ICS) and Operational Technology (OT). When selecting encryption algorithms, it’s crucial to balance security requirements with the operational constraints typical of industrial environments. Let's explore the key encryption algorithms used, their properties, and considerations for their application in ICS/OT.
Symmetric Key Encryption
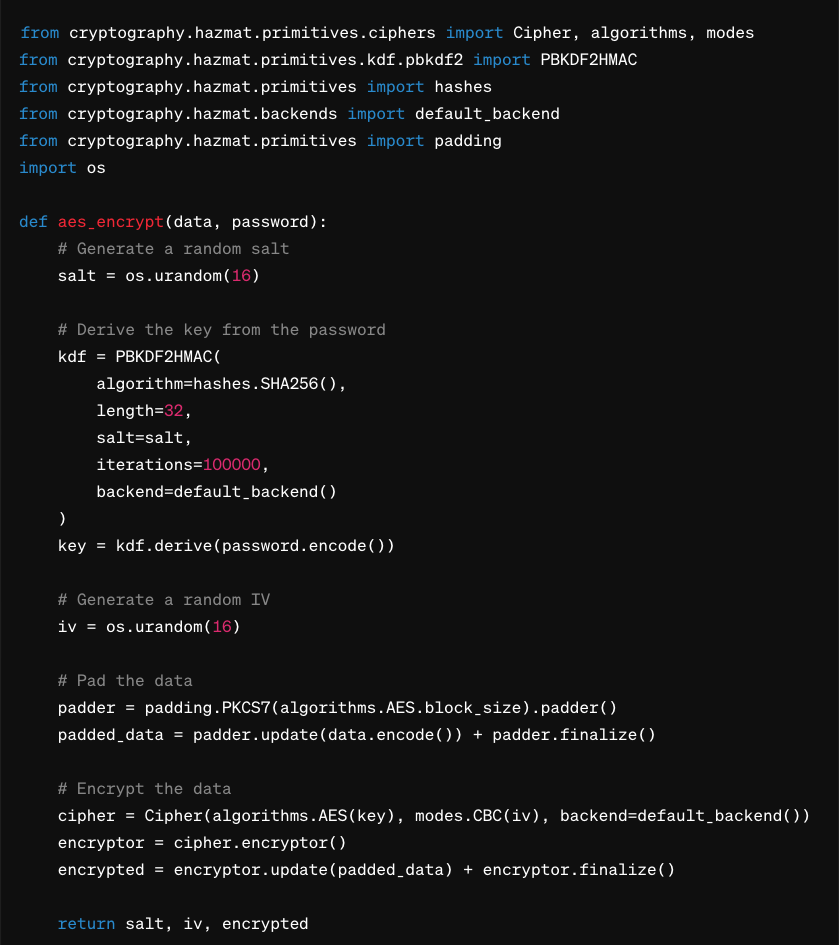
Advanced Encryption Standard (AES)
AES is the most widely used symmetric encryption algorithm, ideal for its strong security and high-performance balance.
It supports key sizes of 128, 192, or 256 bits, making it versatile for different security requirements.
AES is suitable for encrypting large volumes of data at rest in industrial applications, such as archived operational data stored in Level 3 or Level 4 devices. It is also used to encrypt data in transit within secure channels across the network.
AES can be efficiently implemented in hardware and software, but using it in real-time applications requires careful testing to ensure that encryption/decryption processes do not introduce unacceptable delays.
This example can be a foundational guide for encrypting sensitive data in Industrial Control Systems (ICS) and Operational Technology (OT) environments.
Remember, this example is simplified for educational purposes and should be adapted and secured according to your specific operational and security needs.
AES Encryption in Python
AES (Advanced Encryption Standard) is a robust symmetric encryption algorithm commonly used to secure data. This example uses the Cryptography library in Python to perform AES encryption and decryption.
Triple Data Encryption Standard (3DES)
3DES applies the DES cipher algorithm three times to each data block. While slower and less secure than AES, it remains in use in legacy systems where upgrading cryptographic capabilities is challenging.
3DES may still be found in older ICS environments, particularly at Level 2, where upgrading legacy control systems can be disruptive and costly.
Given its vulnerabilities and the availability of more secure algorithms like AES, 3DES is generally recommended as a replacement in modernizing ICS environments.
DES (Triple Data Encryption Standard) is an older encryption method that applies the DES cipher algorithm three times to each data block. It's generally used in legacy systems where updating cryptographic capabilities to more modern standards like AES may not be feasible.
Python Code for 3DES Encryption:
Asymmetric Key Encryption
RSA (Rivest–Shamir–Adleman)
RSA is one of the earliest public-key cryptosystems widely used for secure data transmission. Due to its computational intensity, it’s primarily used for key exchange and digital signatures rather than direct data encryption.
RSA is appropriate for establishing secure communications between servers at Level 4 and SCADA systems at Level 3 by exchanging keys used for symmetric encryption.
RSA's security is based on the factorization of large integers, and critical lengths typically range from 2048 to 4096 bits for adequate security. RSA operations can be slow, so they're generally not used for bulk data encryption.
An example in Python is already shown above.
Elliptic Curve Cryptography (ECC)
ECC offers the same level of cryptographic strength as RSA but with smaller key sizes. This reduces processing overhead and makes it ideal for use in environments with limited resources.
ECC is increasingly used in industrial applications for secure device authentication and key agreement, particularly in embedded systems within Level 2.
ECC requires careful implementation to avoid vulnerabilities associated with poor random number generation or weak curve parameters.
Hash Functions
SHA-256 and SHA-3
Secure Hash Algorithms (SHA) are used to create unique, fixed-size hash values from variable-size transaction inputs. While not encryption algorithms per se, they are crucial for ensuring data integrity and supporting encryption protocols.
Hash functions are used extensively in digital signature applications and form the basis for integrity verification at all levels of the Purdue Model.
SHA-256 is part of the SHA-2 family and provides adequate security for most applications, but SHA-3 is available as a backup against potential future vulnerabilities in SHA-2.
Choosing the correct encryption algorithm and implementing it correctly is critical for protecting sensitive data within ICS and OT environments. Each layer of the Purdue Model presents unique challenges and requirements for encryption. By understanding these details and using appropriate cryptographic solutions, organizations can enhance their overall security posture while maintaining the reliability and efficiency of their industrial operations.
A New Approach to Encryption in ICS/OT Integrating Modern Technologies and Strategies
Integrating VeraCrypt for Non-Real-Time Critical Data
Given its robust encryption capabilities, VeraCrypt can be effectively used at Levels 3 and 4 to encrypt non-real-time critical data such as archived logs, backups, and other sensitive data that do not require immediate access. By implementing VeraCrypt, organizations can ensure the confidentiality and integrity of their data without impacting the performance of critical real-time control systems.
The landscape of Industrial Control Systems (ICS) and Operational Technology (OT) is rapidly evolving, driven by the increased connectivity and the integration of more sophisticated IT technologies. However, this evolution also brings new cybersecurity challenges, particularly ensuring data confidentiality and integrity. While effective, traditional encryption strategies often must fully address the unique operational constraints and security requirements of modern ICS/OT environments. A new approach incorporating advanced encryption technologies and adapting to these systems' specific needs is crucial.
Here's a deeper look into how this can be achieved.
Adaptive Encryption Framework
The Adaptive Encryption Framework (AEF) involves dynamically adjusting encryption methods and policies based on the operational context and the system's security posture. This approach can help manage the real-time balance between security and performance, which is critical in ICS/OT environments.
Key Components of AEF
Context-Aware Security
Encryption mechanisms can be adjusted based on current network conditions, the type of data being processed, and specific threats detected. For example, lighter or heavier encryption algorithms can be used based on the criticality of data and current system load.
Dynamic Key Management
It implements advanced critical management solutions that can handle frequent key changes and ensure that keys are securely distributed and stored. Considering the future threats quantum computing poses, this might include using quantum-resistant algorithms for key generation and exchange.
Integration with Industrial Protocols
Ensuring the encryption solutions are fully compatible with standard industrial protocols such as Modbus, DNP3, and OPC UA. This might involve developing protocol-specific security extensions or wrappers that provide encryption without altering the core protocol functionality.
Leveraging Advanced Cryptographic Techniques
Modern cryptographic techniques can offer advantages over traditional methods for securing ICS/OT systems.
Homomorphic Encryption
This allows for computations to be performed on encrypted data, returning an encrypted result that, when decrypted, matches the result of operations performed on the plaintext. This is particularly useful for cloud-based ICS data analytics and monitoring without exposing the data.
Post-Quantum Cryptography
As quantum computing becomes more common, it is essential to start integrating algorithms that are resistant to quantum attacks. These algorithms are designed to operate effectively on conventional computer systems while providing security against quantum computers.
Zero Trust Architecture
Implementing Zero-Trust principles, where encryption is one of the foundational elements. Every device and transaction is authenticated and encrypted, irrespective of its location within the network hierarchy.
Implementation Example with VeraCrypt and Modern Techniques
Consider a scenario where sensitive ICS data needs to be archived securely while remaining accessible for analysis under specific conditions:
This script demonstrates generating a cryptographic key using Scrypt, a modern key derivation function resistant to brute-force attacks. This key can then be used with VeraCrypt to encrypt disks or data securely, which is suitable for backup or archival purposes.
As ICS/OT environments continue to merge more closely with information technology and face increasing cyber threats, encryption approaches must also evolve. By incorporating adaptive frameworks, leveraging advanced cryptographic techniques, and ensuring compatibility with industrial protocols, it is possible to significantly enhance the security posture of these critical systems without compromising their operational integrity. The future of ICS/OT security lies in adaptive, integrated, and robust cryptographic solutions that protect against current threats and are designed to tackle emerging challenges.
Conclusion: Charting the Future of Encryption in ICS/OT Environments
Applying appropriate encryption strategies in ICS/OT environments requires a thorough understanding of the operational and security needs at each level of the Purdue Model. By carefully selecting and implementing encryption technologies, organizations can protect sensitive industrial data from emerging cyber threats while ensuring operational integrity and compliance with industry regulations. The examples and strategies discussed provide a foundation for securing industrial networks and pave the way for integrating advanced encryption solutions like VeraCrypt in suitable scenarios.
As we look towards the future of encryption in Industrial Control Systems (ICS) and Operational Technology (OT) environments, it's clear that integrating advanced encryption strategies is beneficial and necessary. The increasing sophistication of cyber threats and the expanding connectivity of industrial systems demand a proactive and dynamic approach to cybersecurity. This conclusion will explore the key takeaways from the discussed advanced encryption practices and outline strategic directions for effectively safeguarding ICS/OT infrastructures.
Key Takeaways
Holistic Security Posture
Encryption is critical but must be part of a holistic security approach that includes physical security, network segmentation, and rigorous access controls. The Adaptive Encryption Framework (AEF) proposes a method to dynamically adjust encryption based on contextual factors, which can significantly enhance the security lifecycle management in ICS/OT systems.
Context-Aware Encryption
The concept of context-aware encryption—adjusting encryption practices based on the operational context (such as system load, data sensitivity, and threat landscape)—offers a promising path to balance security with performance. For instance, implementing lighter encryption methods during peak operational periods and more robust encryption during off-peak times can optimize security and system efficiency.
Future-proofing with Advanced Cryptography
Embracing advanced cryptographic techniques, such as homomorphic encryption and post-quantum cryptography, prepares ICS/OT environments for future threats, including those posed by quantum computing. Early adoption and integration of these technologies can provide a competitive edge and ensure long-term resilience against evolving cyber threats.
Regulatory Compliance
As industries increasingly face strict regulations governing data protection and privacy, encryption becomes more critical. Implementing robust encryption strategies secures data and ensures compliance with international standards and regulations, protecting organisations from legal and financial penalties.
Integration Challenges
While integrating advanced encryption technologies presents numerous benefits, it poses challenges, particularly in legacy systems standards in industrial environments. Upgrading these systems to support modern encryption can be costly and complex, requiring a phased approach prioritising critical assets.
Strategic Directions
Invest in Education and Training
As encryption technologies evolve, so must the skills of those tasked with implementing and managing these systems. Investing in ongoing education and training for cybersecurity personnel is essential to stay ahead of the curve in encryption practices.
Develop and Adopt Industry Standards
Industry-wide standards must be developed and adopted for encryption technologies to be effectively implemented across diverse ICS/OT environments. These standards should address the technical aspects of encryption and interoperability, as well as management and compliance issues.
Leverage AI and Machine Learning
Artificial intelligence (AI) and machine learning (ML) can enhance the Adaptive Encryption Framework by enabling more sophisticated security data analysis and automated real-time adjustment to encryption configurations based on detected threats and anomalies.
Strengthen Collaboration Between IT and OT
Bridging the gap between IT and OT teams is crucial for implementing effective encryption strategies. Collaboration ensures that encryption solutions are designed with an understanding of operational requirements and constraints, facilitating smoother integration and operation.
Continuous Improvement and Innovation
Finally, the field of cybersecurity is one of constant change and evolution. Organisations must commit to continuous improvement and innovation in their encryption practices to keep pace with advancing technology and emerging threats.
Final Thoughts
As we advance, the importance of encryption in protecting critical industrial operations cannot be overstated. By adopting a forward-looking approach incorporating adaptive encryption strategies and preparing for future technological shifts, ICS/OT environments can achieve enhanced security and improved compliance and operational efficiency. The path forward involves embracing change, investing in technology, and fostering a culture of security-first thinking across all levels of the organisation.
By Rodrigo Mendes Augusto